The F5 BIG-IP has a template for Exchange 2010 which assists administrators with configuring load balancing for Outlook Anywhere, Active Sync and Outlook Web App. This template does not configure SMTP load balancing. There are many circumstances where you may want an SMTP endpoint IP address to be highly available and load balanced between multiple hub transport servers.
In this post I will go through and show you how to configure the BIG-IP LTM for load balancing the SMTP protocol and the challenges associated with this. This article was written using the F5 BIG-IP LTM VE version 10.2.3.
Create a Health MonitorCreate a health monitor which monitors the Exchange 2010 SMTP service on our Exchange 2010 servers. The heath monitor will send SMTP HELO requests on a regular basis to ensure the SMTP servers are healthy.
Expand Local Traffic and click Add next to Monitors.
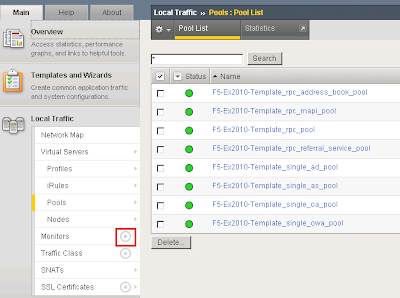
I called the monitor SMTP_Monitor. Set the Type to SMTP. Provided an interval of 120 seconds meaning the monitor will send an SMTP HELO every 2 minutes to the Ex2010 servers to see if they are still online. Configured the Alias service port to 25.
 Create a Pool for the SMTP Servers
Create a Pool for the SMTP ServersA load balancing pool is a logical set of devices, in our case SMTP servers, that you group together to receive and process traffic. To create a new pool under Pool List click Add.
I called the pool smtp_pool. Select the SMTP_Monitor we created earlier. Select the load balancing method as Round Robin. Add the SMTP servers to our pool in which we wish to distribute inbound SMTP connections to.
 Create an SMTP Virtual Server
Create an SMTP Virtual ServerCreate an SMTP Virtual Server on the F5 BIG-IP which will allow the BIG-IP system to listen on TCP25 to load balance incoming SMTP sessions. To do this under Virtual Servers --> Virtual Server List click add.
I called the SMTP Virtual Server SMTP_VS. Under Destination I specified 172.16.51.174. This is the Virtual IP the BIG-IP will listen on for incoming SMTP traffic. Select a service port of 25 and place the device in an enabled state.
Under configuration set SNAT Pool to Auto Map (I have explained what Auto Map is below).
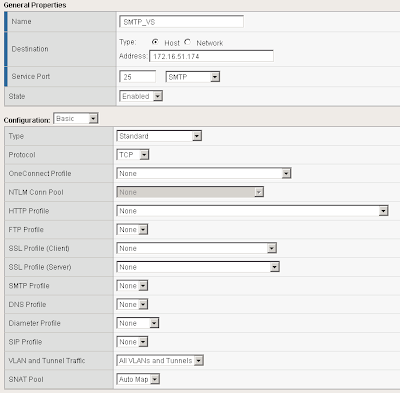
Scroll down further and under resources set the Default Pool to smtp_pool along with the default persistence profile to source_addr.
 Test our BIG-IP SMTP Virtual Server
Test our BIG-IP SMTP Virtual ServerThe F5 BIG-IP device should now be configured to load balance SMTP requests between the two Exchange 2010 servers. In your Virtual Server List the SMTP_VS should come up green.
From a command prompt verify you can telnet our SMTP virtual server on 172.16.51.174 on port 25.
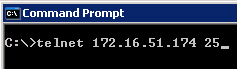
We can see that it successfully connected to one of the SMTP servers in our load balancing pool "smtp_pool"
 At this point your F5 BIG-IP is successfully load balancing SMTP.The Problem...
At this point your F5 BIG-IP is successfully load balancing SMTP.The Problem...When building an email solution it is absolutely critical to avoid becoming an open SMTP relay. Most organisations implement relay restrictions by locking anonymous relay down to certain source IP addresses on their internal network such as applications and printers. Source IP is generally the preferred method as Administrators do not have to deal with SMTP authentication methods. The list of IP addresses who are allowed relay anonymously are usually configured on the Exchange SMTP receive connectors. However when dealing with load balancers such as a F5 BIG-IP Local Traffic Manager this becomes a difficult task.
Why?
Whilst load balancing connections the F5 BIGIP uses SNAT to re-write the source IP address on the SMTP packets to one of its "Self IP" addresses or "Virtual IP" addresses. This means the Exchange servers will see all requests coming from the same IP address making it impossible to determine which request belongs to what client. This is illustrated in the following diagram:
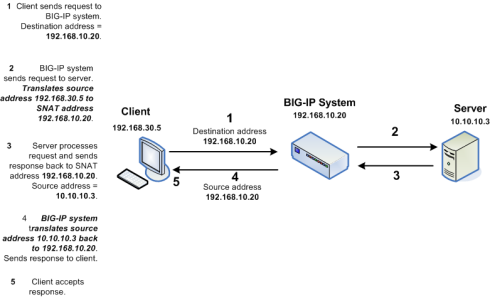
However I have a workaround for you. If we setup two SNAT addresses on the F5 BIG-IP for example 172.16.51.174 and 172.16.51.175 we can configure our BIG-IP to say any source IP addresses that need to be an anonymous open relay hit our Exchange 2010 servers from 172.16.51.174
ELSE hit our Exchange 2010 servers from 172.16.51.175. This solution means we need to configure our list of allowed IP addresses for SMTP relay on our F5 BIG-IP instead of our Exchange SMTP Receive Connectors.
Create a Data Group ListFirst we must create a list of IP addresses we want to allow anonymous relay for on our F5 BIG-IP. These are the IP addresses we would normally configure on our Exchange receive connectors. To do this we need to create a new data group list.
Add a new data group list by expanding iRules --> Data Group List and clicking the add button.
I called my Data Group List smtp_relay_allowed and specified the IP address 172.16.51.21. You can add as many IP addresses as you want for anonymous relay.
 Create a new iRule
Create a new iRuleAn iRule is a powerful and flexible feature of BIG-IP devices which provide you with unprecedented control to directly manipulate and manage any IP application traffic. By creating an iRule we can instruct the BIG-IP to return a different SNAT address based on on the condition. We want to instruct our BIG-IP to perform the following:
IF a clients source IP is on our Data Group List
THEN use an SNAT address of 172.16.51.174
ELSE use the SNAT address of 172.16.51.175.
To create the iRule under Local Traffic Select iRule --> iRule List and click the add button.
I called my iRule smtp_irule and created the following code to perform my required conditions as mentioned above.
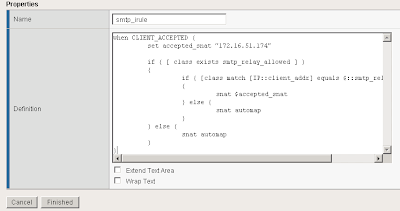
A copy of the code:
when CLIENT_ACCEPTED {
set accepted_snat "172.16.51.174"
if { [ class exists smtp_relay_allowed ] }
{
if { [class match [IP::client_addr] equals $::smtp_relay_allowed] }
{
snat $accepted_snat
} else {
snat automap
}
} else {
snat automap
}
}Automap is a feature of the BIGIP where it automatically selects a Self IP at random to use for the SNAT translation. A Self IP is an IP you have assigned to the BIGIP manually under your network configuration. This is different to a Virtual IP address which is created when you setup a virtual server. I only have one Self IP on my BIG IP set to 172.16.51.175 and one virtual IP set to 172.16.51.174 used by all my F5 virtual servers on different TCP ports. As a result automap will ONLY select 172.16.51.175.
Why would you want multiple source SNAT IP addresses?
For each connection made from the BIG-IP to your load balanced servers a TCP source port needs to be opened for the communication. TCP only has 65535 ports for source and destination traffic so if the number of connections exceeded the number of available ports, the BIG-IP would not be able to take new connections. In this event you could add an additional Self IP and rely on the Automap feature or create an SNAT pool which is a predefined list of IP addresses the BIG-IP is allowed to use for SNAT.
I recommend reading the chapter on SNAT configuration from the F5 website:
http://support.f5.com/kb/en-us/products/big-ip_ltm/manuals/product/ltm_configuration_guide_10_0_0/ltm_snat.htmlHow do I configure Exchange 2010:
On your Exchange 2010 servers create your two receive connectors as normal. Create one receive connector configured for your anonymous relay and setup yoru default receive connector for all other SMTP traffic. Both receive connectors must listen on port 25. Do this on all Exchange servers in your pool.
For information on how to configure your application receive connector for anonymous relay follow this blog post:
http://clintboessen.blogspot.com/2009/07/allow-network-applications-to-relay.htmlApply my new iRule to the SMTP Virtual ServerNext we need to attach the iRule to the SMTP virtual server in the F5 configuration screen. To do this go to your Virtual Servers --> Click Virtual Server List then select our SMTP_VS created earlier.
Select Resources then under iRules click Manage.
Select our smtp_irule out of the list available then click finish.
 Testing our Configuration
Testing our ConfigurationSo time to test the configuration to ensure it works as configured. Lets telnet my BIG-IP SMTP Virtual Server from the host we allowed 172.16.51.23 by running the following command:
telnet 172.16.51.174 25
I then wrote some random comments in the telnet session so we can identify our server 172.16.51.23 in our SMTP logs.
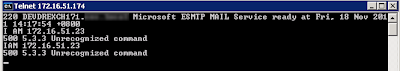
I then repeated the procedure from another server which is not in our Data Group List created above.
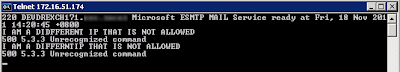
In our SMTP logs on our Exchange 2010 server as expected the 172.16.51.23 server came from 172.16.51.174 and the non trusted IP came from 172.16.51.175.